Octopus Deploy 3.11 upwards has a nice new feature to manage SSL certificates that makes it simple to deploy a web app with its x509 SSL certificate in a secure manner. Once it’s setup the developer and deployer don’t even need access to the certificate or admin rights of the web server – all of it is managed and secured by the Octopus server itself.
Load the certificate into Octopus
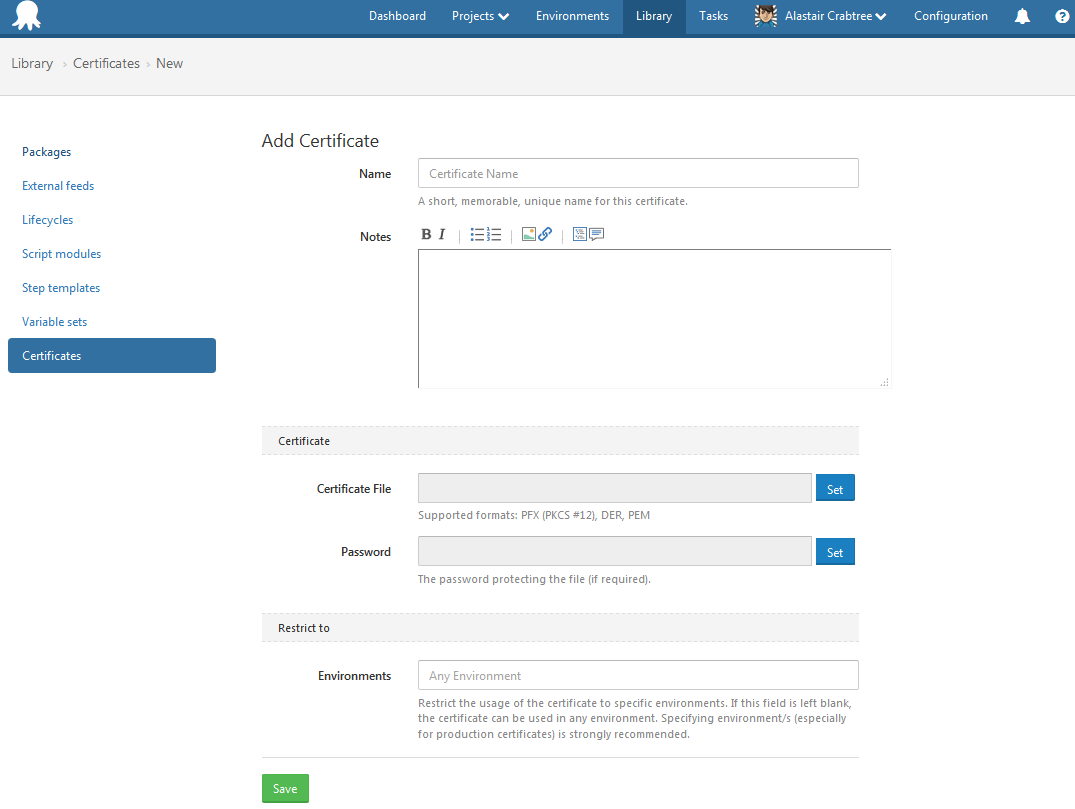
Whether they are internal of public someone needs to load the PFX certificate file into the Octopus Certificate Library. If you just need a wildcard sub-domain certificate like *.example.com then you can even reuse one certificate for multiple sites. Certificate management is a separate role in Octopus security so only appropriate users may have permission to these important bits of your security infrastructure. In addition the certificate can, and probably should, be restricted to the appropriate environment, say TEST or PRODUCTION. Once uploaded, the certificate is now available to all projects and you can even setup a “subscription” to get notified when it is expiring if you wish.
Add an “Import certificate” step to the deploy process
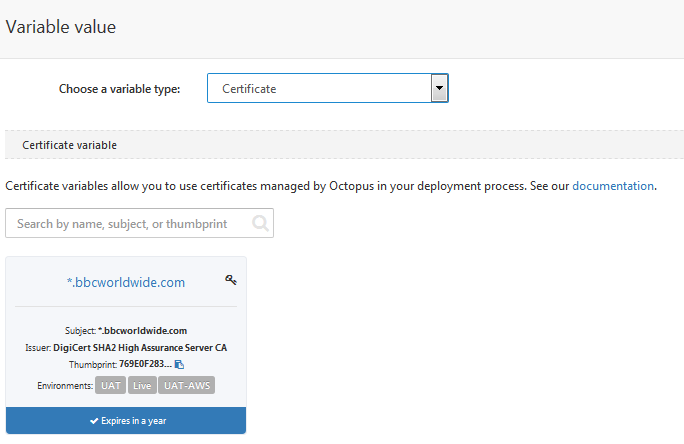
Certificates are made available to the project through variables so create a new variable of new type Certificate and reference the certificate previously uploaded. This allows the certificate to be scoped to machine or environment as you need like other variables.
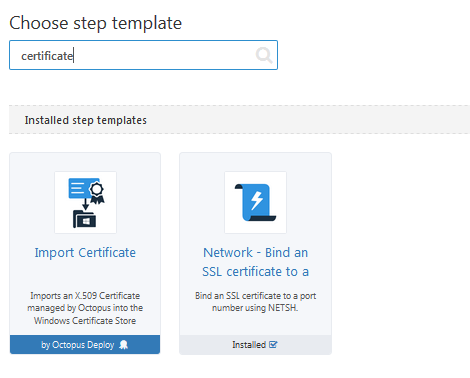
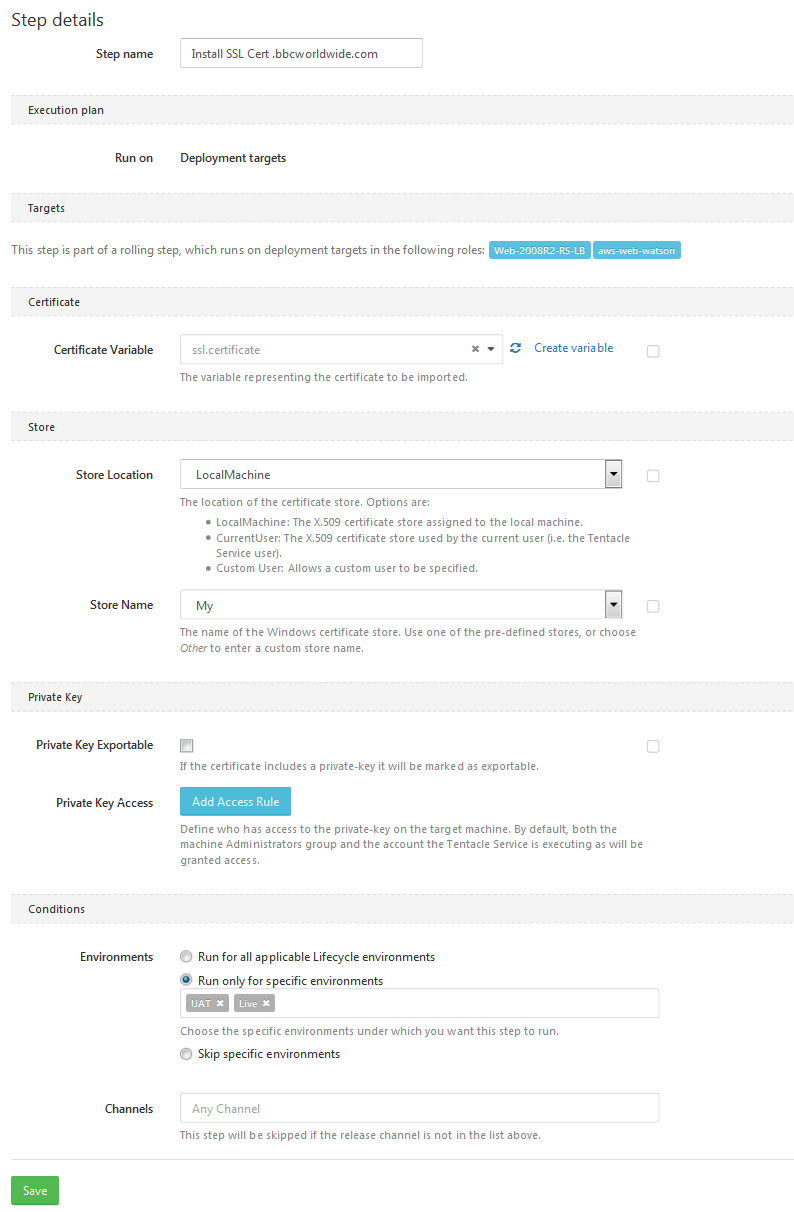
Next add a new step to the deploy process before the actual deploy website step and select the Import Certificate step type.
Specify the certificate variable you just created and leave the rest of the defaults - “LocalMachine” location, “My” Store - as they are all very sensible. This will store the certificate in the Windows Local Machine certificate store, under the Personal certificate folder which is what you want for IIS.
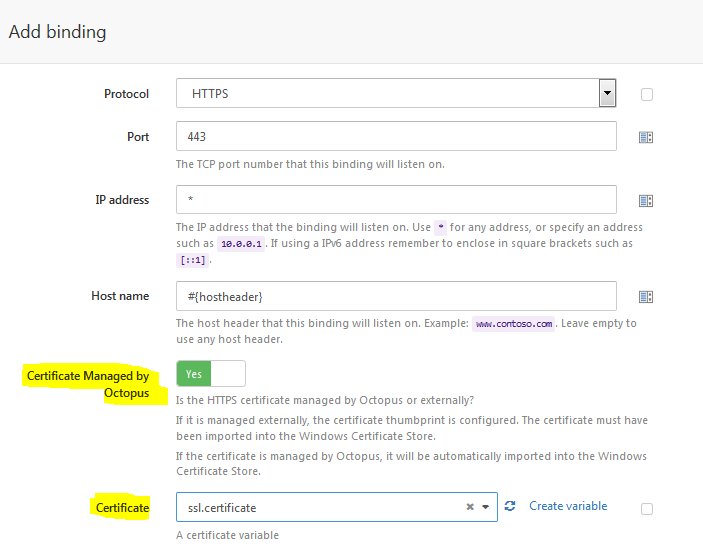
Use the thumbprint when Binding on port 443
Lastly when you are adding an IIS binding on port 443 for SSL during the Deploy Website step you can reference the thumbprint of the certificate that has just been deployed on the server.
Now go deploy secure websites
And that’s it, much easier than managing the certificates with PowerShell and much easier to update them when they expire.